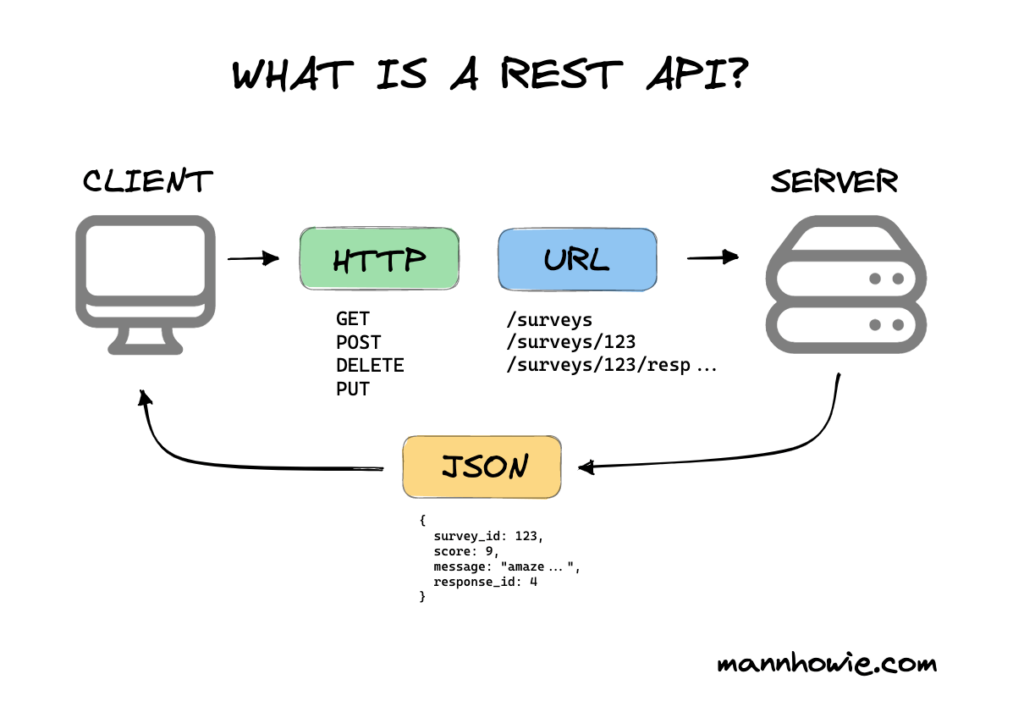
Developing secure REST APIs in C# is essential for ensuring the confidentiality, integrity, and availability of data in modern web applications. By utilizing best practices in authentication, authorization, input validation, and encryption, developers can protect their APIs from common vulnerabilities such as SQL injection, cross-site scripting, and unauthorized access. This not only safeguards sensitive information but also establishes trust with users and clients. In this guide, we will explore the key principles and techniques for building secure REST APIs in C# that adhere to industry standards and promote data security.
Creating secure RESTful APIs is an essential aspect of modern web development. With the increasing popularity of web and mobile applications, it is crucial to ensure that the APIs powering these applications are secure and protect sensitive data from unauthorized access.
Best Practices for Developing Secure REST APIs in C#
When developing REST APIs in C#, following these best practices will help ensure the security of your APIs and protect your users’ data:
1. Implement Authentication and Authorization
Authentication is the process of verifying the identity of users, while authorization determines what actions they are allowed to perform. Implementing authentication and authorization mechanisms, such as JWT (JSON Web Tokens) or OAuth, adds an extra layer of security to your API endpoints.
By using these mechanisms, you can ensure that only authenticated and authorized users can access sensitive data or perform specific actions.
2. Input Validation
Input validation is essential to prevent attacks such as SQL injection or cross-site scripting (XSS). Validate and sanitize all user input to ensure that it meets the expected format and is safe to use.
Using libraries like Microsoft’s AntiXSS or input validation frameworks like FluentValidation can help you implement robust input validation for your REST APIs.
3. Use HTTPS
Always use HTTPS (HTTP Secure) for your REST APIs. HTTPS encrypts the data transmitted between the server and the client, ensuring its confidentiality and integrity.
Obtain an SSL/TLS certificate and configure your web server to enable HTTPS. This will help protect sensitive data and prevent man-in-the-middle attacks.
4. Role-Based Access Control
Implement role-based access control (RBAC) to define different levels of access for different user roles. With RBAC, you can assign specific permissions to roles and control what actions each role can perform.
By implementing RBAC, you can ensure that only authorized users with the required roles can access and modify specific resources.
5. Protect Against Cross-Site Request Forgery (CSRF)
CSRF attacks occur when unauthorized commands are executed on behalf of an authenticated user. To protect against CSRF attacks, ensure the use of anti-forgery tokens in your REST APIs.
By including anti-forgery tokens in each request, you can verify that the requests originated from your trusted application and not from a malicious source.
Developing Secure REST APIs in C# – Tips and Examples
Here are some tips and examples that will further help you develop secure REST APIs in C#:
TIP: Use Secure Password Storage
When storing user passwords, it is essential to store them securely. Use strong one-way hashing algorithms, such as bcrypt or PBKDF2, to hash and salt passwords.
Never store passwords in plain text or use weak hashing algorithms like MD5 or SHA1. Securely hash passwords to prevent unauthorized access if your database is compromised.
EXAMPLE: User Authentication and JWT
Here’s an example of how you can implement user authentication using JWT in your C# REST API:
“`csharp
[HttpPost]
public IActionResult Authenticate([FromBody] LoginModel model)
{
// Validate user credentials here
if (/* User authentication succeeds */)
{
var token = GenerateJWTToken();
return Ok(new { token });
}
return Unauthorized();
}
“`
In this example, the `Authenticate` endpoint receives a `LoginModel` object containing the user’s credentials. After validating the credentials, you can generate a JWT token using a library like System.IdentityModel.Tokens.Jwt.
TIP: Implement Rate Limiting
Rate limiting can help protect your REST APIs from abuse and DDoS attacks. By implementing rate limiting, you can limit the number of requests a client can make within a specific timeframe.
Use libraries like AspNetCoreRateLimit or implement custom rate-limiting mechanisms based on IP addresses or API keys to prevent excessive requests.
EXAMPLE: Protected API Endpoint
Here’s an example of how you can protect an API endpoint in C# using authentication and authorization:
“`csharp
[HttpGet]
[Authorize(Roles = “Admin”)]
public IActionResult GetSensitiveData()
{
// Retrieve and return sensitive data here
return Ok(sensitiveData);
}
“`
In this example, the `GetSensitiveData` endpoint is protected and can only be accessed by users with the “Admin” role. By adding the `[Authorize(Roles = “Admin”)]` attribute, you can restrict access to authorized users only.
TIP: Logging and Monitoring
Implement robust logging and monitoring mechanisms for your REST APIs. Log important events and errors to track potential security breaches or suspicious activities.
Use tools like Serilog or Application Insights to centralize and analyze your logs, enabling you to detect and respond to security incidents in a timely manner.
In this tutorial, we discussed the best practices for developing secure REST APIs in C#. By implementing authentication and authorization mechanisms, input validation, using HTTPS, and following other recommended practices, you can ensure the security of your APIs.
Remember to always stay up-to-date with the latest security trends and regularly review and update your REST APIs to mitigate any potential security risks.
Developing secure REST APIs in C# is crucial to safeguarding sensitive data and ensuring the integrity of communication between clients and servers. By following best practices such as implementing authentication, encryption, and input validation, developers can enhance the security of their APIs and protect against potential threats. It is imperative to stay informed about the latest security trends and continuously update and improve API security measures to mitigate risks effectively.