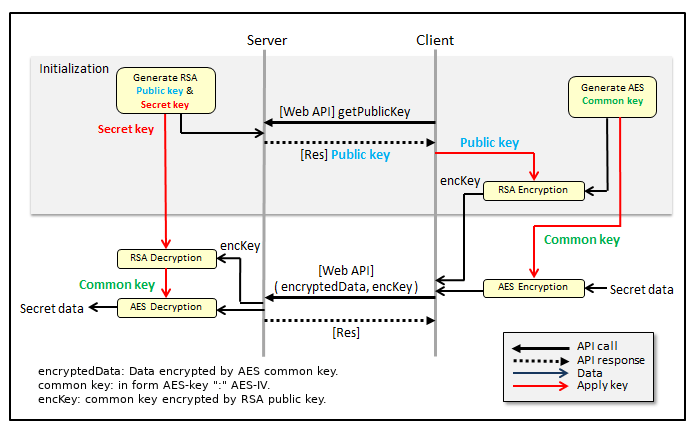
When working with APIs and Web Services, ensuring the security and privacy of data being transmitted is of utmost importance. One common method to achieve this is by implementing data encryption using the Advanced Encryption Standard (AES) algorithm. AES is a symmetric encryption algorithm that can be used to securely encrypt and decrypt data exchanged between API clients and servers. In this guide, we will explore how to incorporate AES encryption in your API implementation to enhance data security and protect sensitive information from unauthorized access.
In today’s digital landscape, ensuring data security is paramount, especially when dealing with APIs and web services. One of the most robust methods for securing data transferred via APIs is through AES (Advanced Encryption Standard), which provides a strong encryption mechanism to protect sensitive information. This article will delve into the implementation of API data encryption using AES, discussing its importance, key concepts, and practical coding examples.
Why Use AES for API Data Encryption?
AES is a symmetric encryption algorithm widely used across the globe, known for its speed and security. Here are some compelling reasons to use AES for encrypting API data:
- Security: AES is deemed highly secure and is trusted by governments and organizations for encrypting sensitive data.
- Performance: Its efficiency makes it suitable for real-time data encryption in APIs.
- Standardization: Being an established standard, it has been rigorously analyzed and widely accepted.
Understanding the Basics of AES Encryption
AES is a symmetric key encryption technique, which means the same key is used for both encryption and decryption. AES supports different key sizes, primarily 128, 192, and 256 bits. The choice of key size impacts the security level and performance of the algorithm:
- AES-128: Provides a high level of security and is typically sufficient for most use cases.
- AES-192: Offers a higher security margin, suitable for applications requiring extended security.
- AES-256: Provides maximum security, often used in applications where protection against potential future attacks is a concern.
Key Components of AES Encryption
Before implementing AES in your API, it’s crucial to understand its key components:
- Plaintext: The original data that needs to be encrypted.
- Ciphertext: The encrypted data that results from applying the AES algorithm to plaintext.
- Key: A secret key used for both encryption and decryption.
- Initialization Vector (IV): An optional component that provides an additional layer of security, ensuring that the same plaintext encrypted with the same key produces different ciphertexts.
Setting Up Your Development Environment
To begin implementing AES encryption for your API, ensure you have the appropriate libraries based on the programming language you are using. Below are some common programming environments and their respective libraries:
- Python: Use the `pycryptodome` library.
- Node.js: The `crypto` module is built-in and can be leveraged for AES.
- Java: The `javax.crypto` package contains all necessary classes for AES.
Implementing AES Encryption in Python
Below is a step-by-step guide on how to implement AES encryption in a Python API:
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
from Crypto.Random import get_random_bytes
import base64
def encrypt_data(plain_text, key):
# Generate a random initialization vector (IV)
iv = get_random_bytes(AES.block_size)
cipher = AES.new(key, AES.MODE_CBC, iv)
# Pad the plaintext to be multiple of block size
padded_text = pad(plain_text.encode(), AES.block_size)
# Encrypting the data
cipher_text = cipher.encrypt(padded_text)
# Combining the IV and Ciphertext for storage/transmission
return base64.b64encode(iv + cipher_text).decode('utf-8')
# Example usage
key = get_random_bytes(16) # AES-128
encrypted_data = encrypt_data("Sensitive API Data", key)
print("Encrypted Data:", encrypted_data)Implementing AES Decryption in Python
To retrieve the original data, the decryption process should mirror the encryption process:
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import base64
def decrypt_data(cipher_text_base64, key):
# Decode from base64
cipher_text = base64.b64decode(cipher_text_base64)
# Extract IV and the actual ciphertext
iv = cipher_text[:AES.block_size]
cipher_text = cipher_text[AES.block_size:]
# Create a new cipher object with the same key and iv
cipher = AES.new(key, AES.MODE_CBC, iv)
# Decrypt the data
padded_text = cipher.decrypt(cipher_text)
# Unpad to get the original plaintext
return unpad(padded_text, AES.block_size).decode('utf-8')
# Example usage
decrypted_data = decrypt_data(encrypted_data, key)
print("Decrypted Data:", decrypted_data)Implementing AES Encryption in Node.js
For Node.js, the process is similar. Here is how to accomplish AES encryption and decryption:
const crypto = require('crypto');
function encryptData(plainText, key) {
const iv = crypto.randomBytes(16);
const cipher = crypto.createCipheriv('aes-128-cbc', key, iv);
let encrypted = cipher.update(plainText, 'utf8', 'base64');
encrypted += cipher.final('base64');
// Combine IV with ciphertext for storage
return iv.toString('base64') + ':' + encrypted;
}
function decryptData(encryptedText, key) {
const parts = encryptedText.split(':');
const iv = Buffer.from(parts.shift(), 'base64');
const encryptedTextBuffer = Buffer.from(parts.join(':'), 'base64');
const decipher = crypto.createDecipheriv('aes-128-cbc', key, iv);
let decrypted = decipher.update(encryptedTextBuffer, 'base64', 'utf8');
decrypted += decipher.final('utf8');
return decrypted;
}
// Example usage
const key = crypto.randomBytes(16); // AES-128 key
const encryptedData = encryptData('Sensitive API Data', key);
console.log('Encrypted Data:', encryptedData);
const decryptedData = decryptData(encryptedData, key);
console.log('Decrypted Data:', decryptedData);Common Mistakes to Avoid
When implementing AES encryption in your APIs, there are common pitfalls to be aware of:
- Using a Weak Key: Always use a strong, randomly generated key. Avoid hardcoding keys into your application.
- Not Using an IV: Always use an initialization vector (IV) for CBC mode to enhance security.
- Ignoring Data Padding: Ensure that your data is properly padded before encryption to match the block size.
Testing Your Implementation
Once you have implemented AES encryption and decryption, thorough testing is essential to ensure everything functions as intended. Consider the following:
- Unit Tests: Create unit tests to validate that encryption and decryption produces the original data.
- Performance Testing: Test the performance under varying loads to ensure your API can handle high volume requests securely.
- Security Audits: Regularly evaluate your implementation for any potential vulnerabilities.
Conclusion
By applying AES encryption in your APIs, you take significant steps toward safeguarding sensitive data against potential threats. It is vital to understand the intricacies of encryption, carefully manage keys, and follow best practices to ensure the integrity and confidentiality of your data.
Implementing API data encryption with the Advanced Encryption Standard (AES) is a crucial step in ensuring the security and privacy of data transmitted through APIs and web services. By utilizing AES encryption, sensitive information can be securely protected from unauthorized access and threats. It is essential for developers to carefully integrate AES encryption into their API design to safeguard the integrity and confidentiality of data exchanges in today’s digitally interconnected landscape.